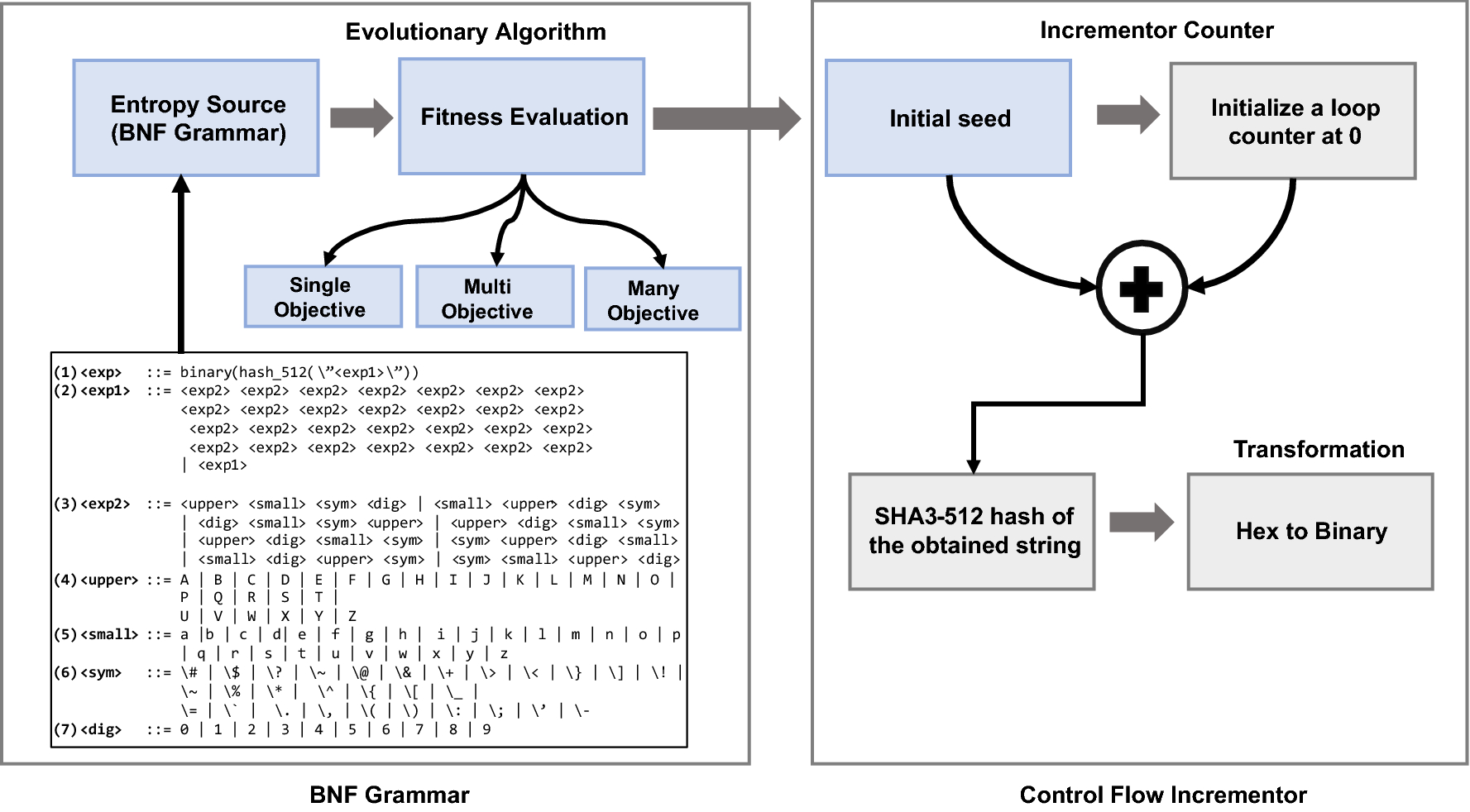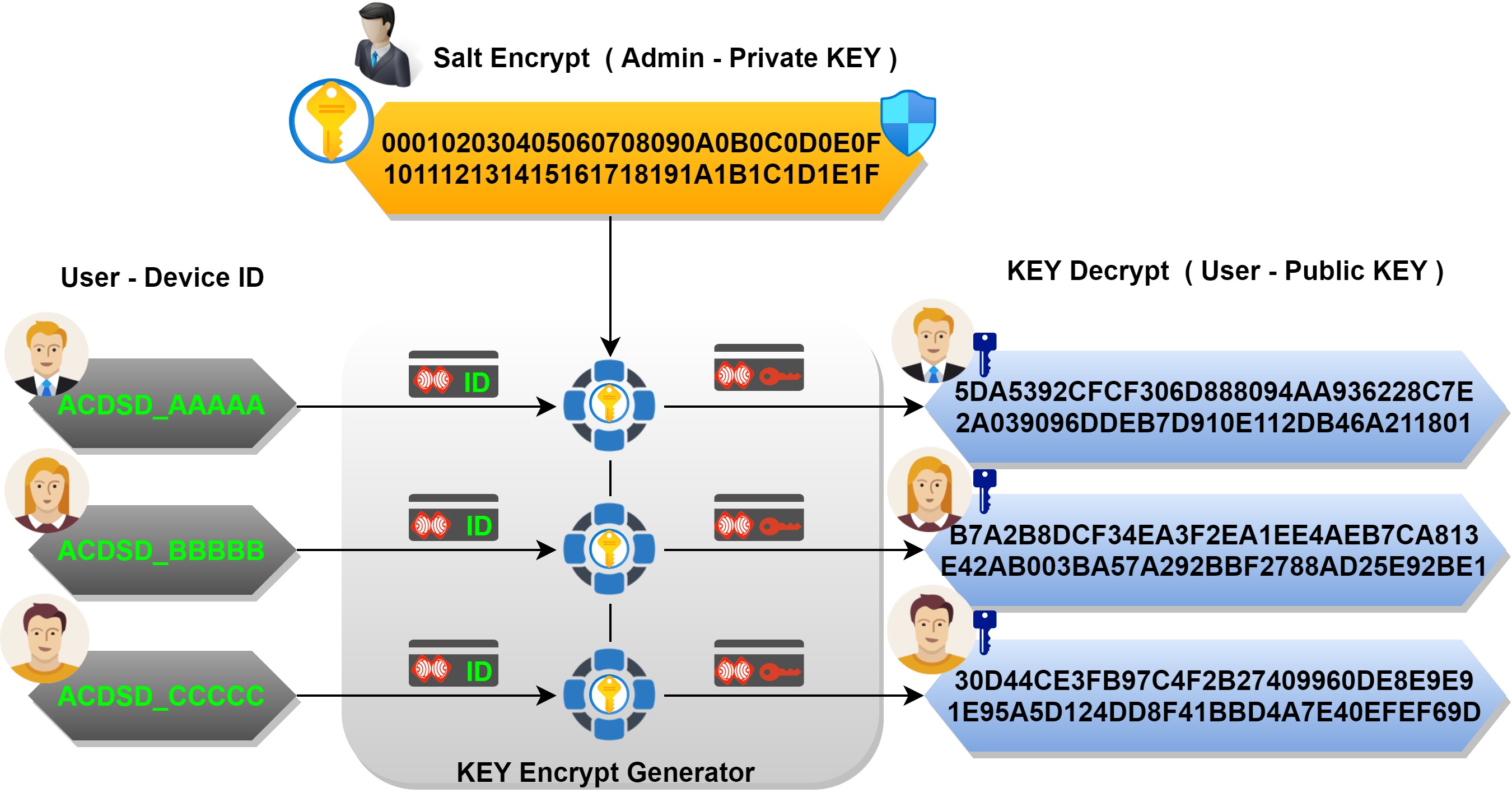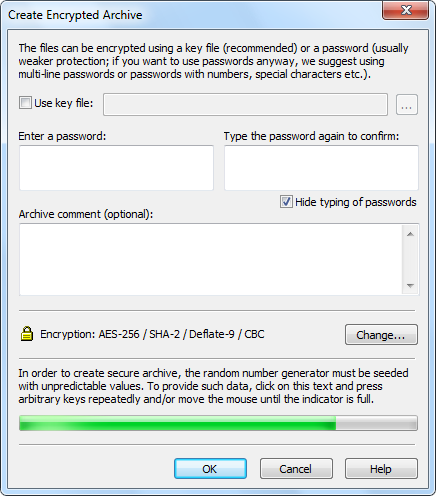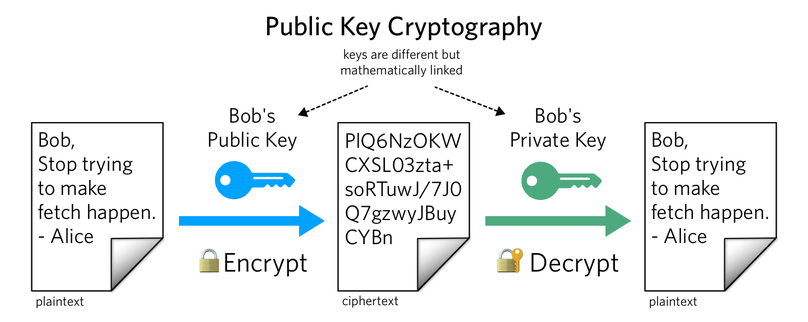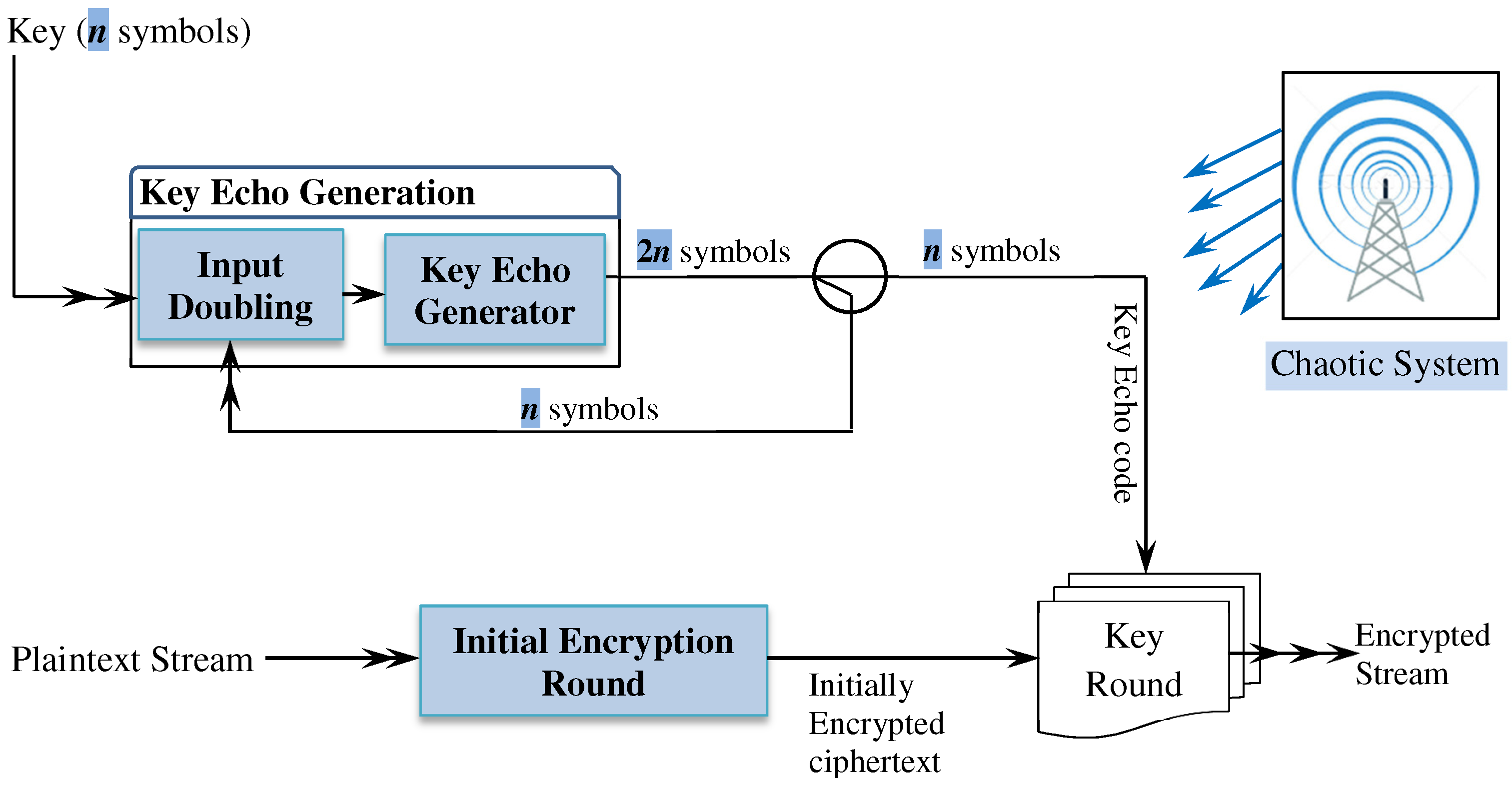
Symmetry | Free Full-Text | Light and Secure Encryption Technique Based on Artificially Induced Chaos and Nature-Inspired Triggering Method

Amazon.com: NordPass 1-Year Premium Password Manager Subscription for 6 Devices - Password Manager Software with Top-Tier Encryption, Data Breach Scanner, Secure Password Sharing, Password Generator

Cjmcu-608 Atecc608a Cryptographic Password Key Memory Storage Iic I2c Random Number Generator Rng Encryption Decryption Module - Integrated Circuits - AliExpress

Example of an embedded encryption scheme: real time image encryption... | Download Scientific Diagram

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress

Password Generator | Encrypting and Decrypting Password with Symmetric Encryption using Python - YouTube